SOPHOS ZERO TRUST NETWORK ACCESS
⇒ What is Zero Trust Network Access?
- Sophos ZTNA (Zero Trust Network Access) is a security solution that provides secure access to applications and resources without relying on a traditional VPN. With ZTNA, users are granted access only to the specific applications or resources they need, based on their identity and other contextual information, rather than having access to the entire network. This approach is based on the Zero Trust security model, which assumes that all network traffic is potentially malicious and should be inspected and verified before being allowed.
- Sophos ZTNA is designed to help organizations provide secure access to their network resources while also ensuring that access is granted only to authorized users and devices. ZTNA accomplishes this by using a combination of identity-based authentication, micro-segmentation, and real-time policy enforcement. ZTNA can be deployed as a cloud-based service or on-premises appliance and can integrate with existing identity and access management (IAM) systems to provide seamless access to resources.
- Sophos ZTNA provides several benefits, including enhanced security, improved user experience, and reduced IT overhead. With ZTNA, users can access their applications and resources from anywhere, without needing to use a VPN or being tied to a specific location. This makes it an ideal solution for organizations with remote or mobile workforces. Additionally, ZTNA provides an extra layer of protection against cyber threats by limiting access to only the necessary resources and validating the identity of users and devices before granting access.
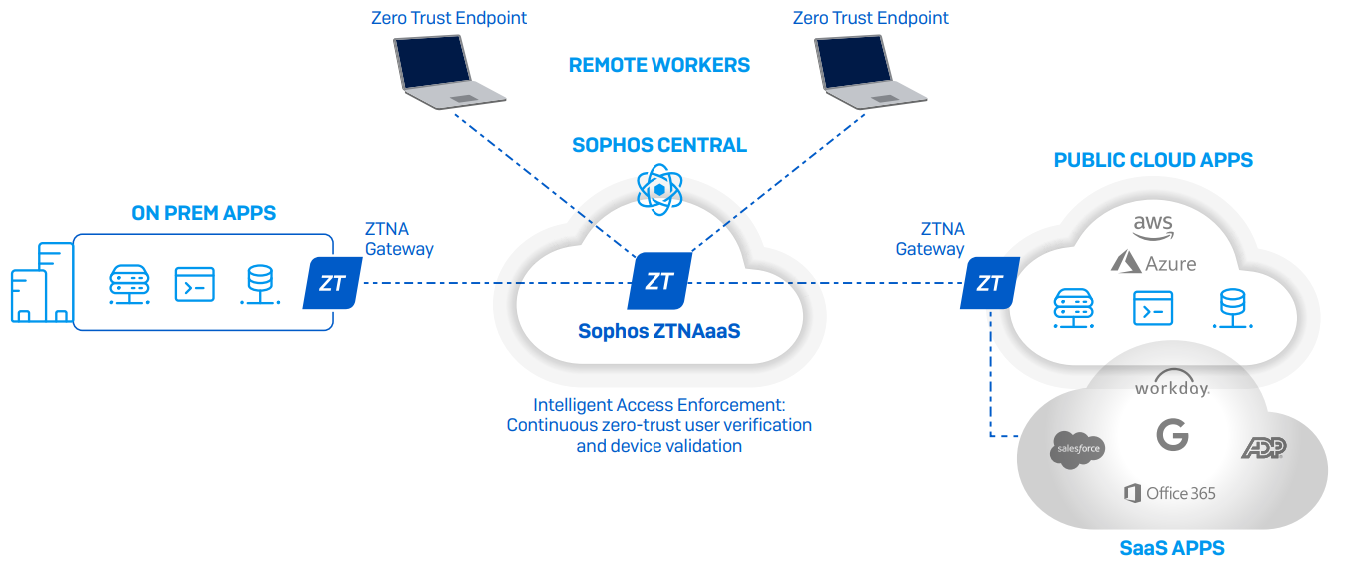
⇒ How it Works Sophos ZTNA
Sophos ZTNA works by providing secure access to corporate applications and resources through a cloud-based intermediary called the Sophos ZTNA service. When a user requests access to an application, the Sophos ZTNA service verifies the user's identity and device posture, then grants access to the application if the user and device meet the defined security requirements.
Sophos ZTNA uses the following steps to provide secure access:
- Authentication: Users are authenticated using multi-factor authentication (MFA) and device certificates.
- Authorization: Access policies are applied based on user identity, device posture, and other contextual information.
- Access: Users are granted access to applications and resources only if they meet the defined security requirements.
- Monitoring: All access is logged and monitored for potential threats and anomalies.
Sophos ZTNA provides secure access to corporate applications and resources without exposing them to the internet, reducing the risk of data breaches and cyber-attacks. It also provides a better user experience by allowing users to access resources from anywhere without needing a VPN or complicated configurations.

⇒ Sophos ZTNA Key Features
- Enable Remote Workers - Remote Access VPN has served us well, but was never designed for this new world. ZTNA provides a much better alternative for remote access by providing better security and threat protection, an easier more scalable management experience, and a more transparent frictionless experience for end-users.
- Micro-Segment Your Applications - With VPN, you’re providing network access. With Sophos ZTNA you’re only providing specific application access. Your applications, users, and devices are micro-segmented and with the integration of device health into access policies, and continuous authentication verification, you get much better security. This eliminates all the implicit trust and the lateral movement that comes along with VPN.
- Control Access to SaaS Apps - As an alternative or supplement to SaaS application-allowed IP ranges, you can utilize ZTNA and your Azure AD identity provider to control access to important SaaS applications – blocking denied devices and unauthorized users from accessing important cloud apps and data.
- Stop Ransomware and Other Threats - Hackers and attackers are leveraging poorly secured remote systems and VPN vulnerabilities to get a foothold on networks to deploy ransomware. Sophos ZTNA helps reduce the surface area and risk of a Ransomware attack by removing a new and growing vector. With ZTNA remote systems are no longer connected “to the network” and only have specific application access.
- Onboard New Apps and Users Quickly - Sophos ZTNA is much leaner, cleaner, and therefore easier to deploy and manage than traditional remote access VPN. It enables better security and more agility in quickly changing environments with users coming and going - making day-to-day administration a quick and painless task and not a full-time job.
- Secure RDP Access - Remote Desktop Protocol is a common tool for remote workers and administrators – but is also one of the most common vectors of attack by bad actors. ZTNA can shield your RDP systems from attacks and provide secure access only to authorized users and devices, including new passwordless options with Microsoft Windows Hello for Business that further helps secure important credentials from possible compromise.

⇒ Top Six Advantages of ZTNA
Zero Trust Network Access (ZTNA) is a security framework that provides secure access to resources based on the principle of "never trust, always verify." Here are six advantages of ZTNA:
Improved Security: ZTNA provides a higher level of security compared to traditional VPNs and other access methods by implementing a more granular and contextual access control system.
Enhanced User Experience: ZTNA uses a more user-centric approach that allows users to access resources from anywhere, on any device, without compromising security.
Reduced Risk of Data Breaches: ZTNA mitigates the risk of data breaches by ensuring that only authorized users and devices have access to resources.
Cost Savings: ZTNA reduces the cost of managing and maintaining VPN infrastructure, hardware, and software licenses.
Simplified Access Management: ZTNA provides a centralized platform for managing access to resources, making it easier to manage user access and permissions.
Compliance: ZTNA helps organizations meet regulatory compliance requirements by providing a more secure and auditable access control system.

⇒ Advanced Vision IT Ltd Cybersecurity Products & Software
To build good cybersecurity protection, you need physical products and software that will help strengthen your network against attacks. If you want to view some of the ADVANCED VISION IT's cyber protection solutions, click on the links below.
- Endpoint security and antivirus software - offer a centralized management system from which security administrators can monitor, protect, and investigate vulnerabilities across all endpoints, including computers, mobile devices, servers, and connected devices. Antivirus software helps keep a computer system healthy and free of viruses and other types of malware.
- Employee Monitoring Solution - Employee monitoring solutions are software tools that enable employers to monitor the activities of their employees while they are at work. These solutions can be used to track employees' computer usage, including their internet browsing history, email communication, keystrokes, and application usage.
- Cybersecurity Backup - A backup is a copy of the system or network's data for file restoration or archival purposes. Backups are an essential part of a continuity of operations plan as they allow for data protection and recovery.
- Еmail Protection - refers to technology designed to prevent, detect and respond to cyber-attacks delivered through email. The term covers everything from gateways email systems to user behavior to related support services and security tools.
- Password Vault Manager - A password vault, password manager, or password locker is a program that stores usernames and passwords for multiple applications securely and in an encrypted format. Users can access the vault via a single “master” password.
- Vulnerability Assessment & Patch Management - The main difference between patch management and vulnerability management is that patch management is the operational process of applying remediations (patches) to vulnerable systems. Vulnerability management is the process of identifying, scanning, and prioritizing vulnerabilities for remediation.
- Data loss prevention (DLP) - makes sure that users do not send sensitive or critical information outside the corporate network.
- Microsoft Office 365 and Azure Backup and Migration - Microsoft Office 365 is a cloud-based suite of productivity and collaboration tools that includes popular applications such as Word, Excel, PowerPoint, and Outlook. Azure Backup and Migration are cloud-based services offered by Microsoft that allow organizations to protect and migrate their data to the cloud.
- Zero Trust Network Access (ZTNA) Solution - Zero Trust Network Access (ZTNA) is a security model that assumes that every user, device, and network connection is potentially insecure and should not be trusted by default. ZTNA replaces traditional perimeter-based security models, assuming that all network users and devices are trusted.
- Cloud Security - Cloud security is a collection of security measures designed to protect cloud-based infrastructure, applications, and data. These measures ensure user and device authentication, data and resource access control, and data privacy protection.
- Next-Generation Firewall - protects your network by filtering traffic and acting as a guard between your internal network and the rest of the world. Without a Firewall, your business systems could be left wide open and vulnerable to attack. It also serves as another protective layer to block malicious software.
- Active Directory Security and Recovery are critical components of any organization's cybersecurity strategy. Here are some key steps that can be taken to secure and recover Active Directory.
- SIEM & SOAR - SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) are both tools used in cybersecurity to monitor and respond to security threats.
⇒ BOUTIQUE MANAGED SERVICES
- Network domain
- Linux domain
- Microsoft domain
- Virtualization domain
- Database domain
- DevOps-as-a-Service
CONTACT OUR TEAM OF PROFESSIONALS FOR A COMPLETELY FREE CONSULTATION
CLAIM YOUR FREE IT AUDIT & CONSULTATION SCHEDULE A CALL WITH OUR TEAM

























