TENABLE SECURITY CENTER
See everything. Predict Vulnerabilities in Advance with Tenable Security Center
⇒ What is Tenable Security Center?
- Tenable.sc are Tenable’s on-premises vulnerability management solutions . Built on industry-leading Nessus technology, the Tenable.sc family of products identifies, investigates and prioritizes vulnerabilities, providing you with a risk-based view of your security and compliance posture.
- Get a risk-based view of your IT, security and compliance posture so you can quickly identify, investigate and prioritize your most critical assets and vulnerabilities.
- Managed on-premises and powered by technology the Tenable.sc suite of products provides the industry's most comprehensive vulnerability coverage with real-time continuous assessment of your network. It’s your complete end-to-end vulnerability management solution .
- Active scanning, agents, passive monitoring, external attack surface management and CMDB integrations provide a complete and continuous view of all of your assets including ones that were previously unknown.
- With coverage for more than 66,000+ vulnerabilities, Tenable has the industry’s most extensive CVE coverage and security configuration support to help you understand your security and compliance posture with confidence.
- Tenable's Predictive Prioritization technology combines vulnerability data, threat intelligence and data science to give you an easy-to-understand risk score so you know which vulnerabilities to fix first.


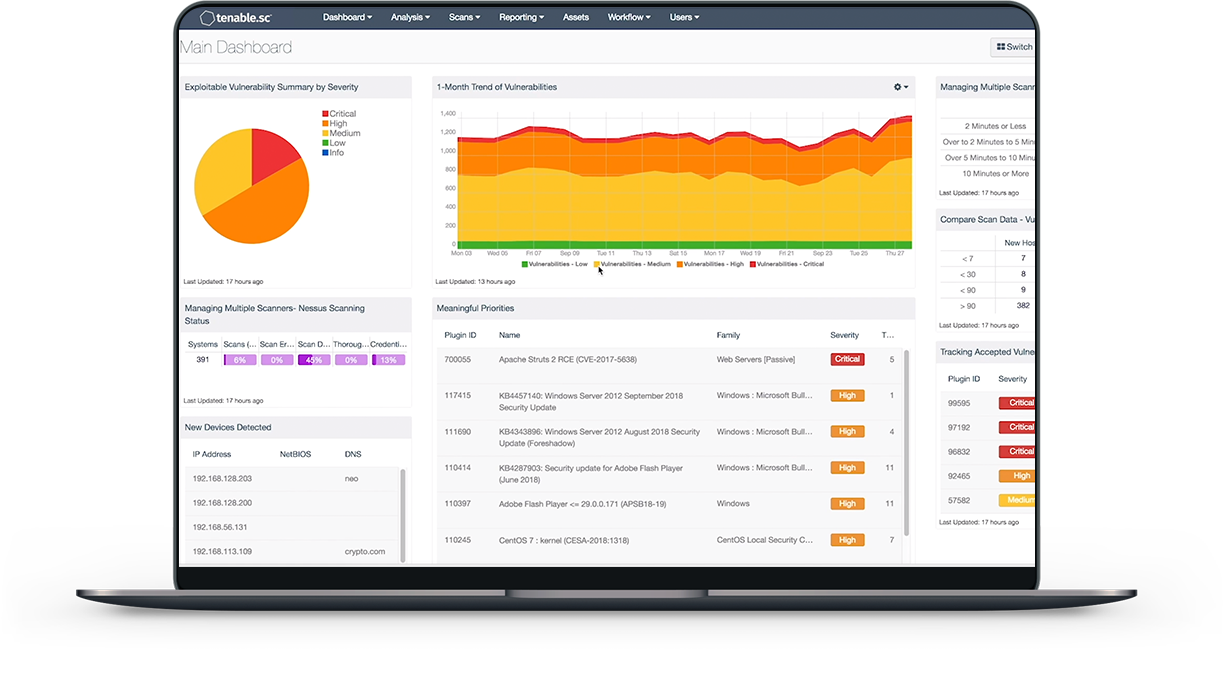
⇒ How Does The Tenable.sc Find Assets and Vulnerabilities?
- Passive monitoring - Monitoring network traffic and events in real-time provides information on which assets are connected to the internet and how they communicate. It identifies new or never-before-seen devices or applications, and detects suspicious behavior as it happens.
- Active scanning - Thoroughly analyzes asset state to identify vulnerabilities, misconfigurations, malware and other weaknesses.
- Host data - Actively monitor host activities and events, including insight into access and changes.
- Intelligent connectors - Leveraging your other security investments, Tenable.sc can integrate additional security data to improve context and analysis. Both will analyze information from a wide range of data sources including Active Directory (AD), configuration management databases (CMDBs), patch management systems, mobile device management (MDM) systems, cloud platforms and more
- Agent scanning - Instantly audit transient or hard-to-scan assets that intermittently connect to the internet without credentials. Once installed, agents can run credentialed scans without ongoing host credentials.
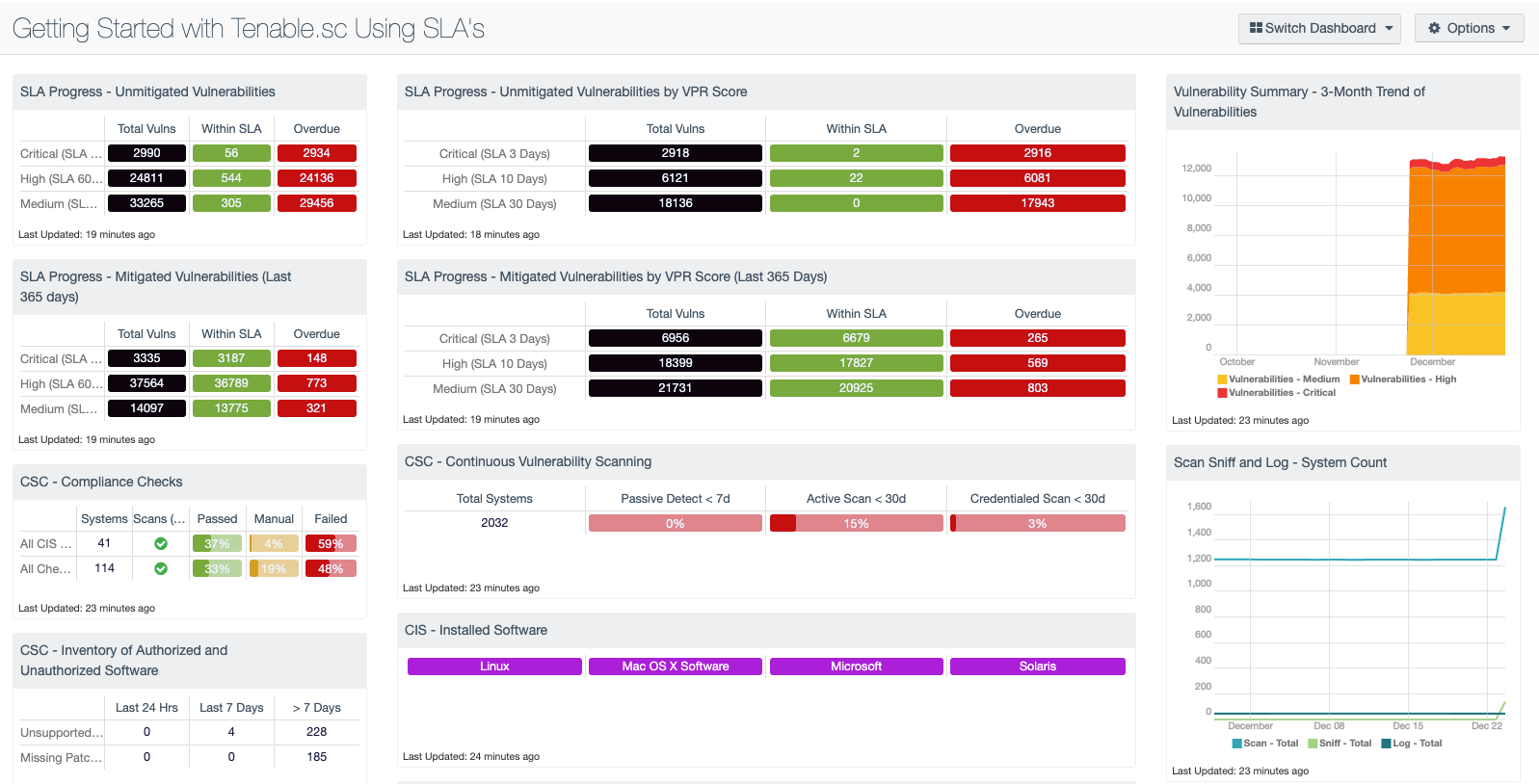
⇒ Actively Identify, Investigate and Prioritize Vulnerabilities
- See Everything - A diverse array of sensors automatically gathers and analyzes your security and compliance data to give you full visibility into your converged attack surface.
- All Your Data Analyzed Continuously - Continuously assess your network for unknown assets and vulnerabilities, and monitor network changes, users, applications, cloud infrastructure and trust relationships so you never miss a beat.
- Predict Dangerous Vulnerabilities - Instantly identify and prioritize vulnerabilities with the highest impact to your organization. Get targeted alerts when new threats appear to quickly begin remediation.
- Predictive Prioritization combines Tenable-collected vulnerability data with third-party vulnerability and threat data and analyzes them together with the advanced data science algorithm Tenable Research developed. Each vulnerability receives a Vulnerability Priority Rating (VPR) that represents the likelihood an attacker may exploit a given vulnerability in the next 28 days along with its severity. You can use VPR to understand actual cyber risk of vulnerabilities in their unique environments so you can prioritize remediation efforts on vulnerabilities with the greatest impact.

⇒ Quickly Measure and Analyze Security and Compliance Risk
- Manage Your Data, Your Way - Tenable.sc is the leading on-prem option for Vulnerability Management. Manage your data your way with on-prem or hybrid deployment options while reducing risk for the organization.
- Understand Asset Criticality - Tenable’s Asset Criticality Rating (ACR) in Tenable.sc provides an added dimension to understanding the criticality of your assets to make better decisions in reducing risk for your organization.
- Get Immediate Insight - Leverage more than 350 pre-built, highly customizable dashboards and reports to get clear, actionable insight into the data you need to easily identify threats.
- Easily Customize - Create different reports for different audiences to ensure the most critical threats are seen and dealt with immediately. Generate reports on demand or schedule them, and automatically share with the appropriate recipients.
- Streamline Compliance Reporting - Stay compliant with immediate visibility into your compliance posture. Easily demonstrate adherence with predefined checks against industry standards and regulatory mandates.

⇒ Advanced Vision IT Ltd Cybersecurity Products & Software
To build good cybersecurity protection, you need physical products and software that will help strengthen your network against attacks. If you want to view some of the ADVANCED VISION IT's cyber protection solutions, click on the links below.
- Endpoint security and antivirus software - offer a centralized management system from which security administrators can monitor, protect, and investigate vulnerabilities across all endpoints, including computers, mobile devices, servers, and connected devices. Antivirus software helps keep a computer system healthy and free of viruses and other types of malware.
- Employee Monitoring Solution - Employee monitoring solutions are software tools that enable employers to monitor the activities of their employees while they are at work. These solutions can be used to track employees' computer usage, including their internet browsing history, email communication, keystrokes, and application usage.
- Cybersecurity Backup - A backup is a copy of the system or network's data for file restoration or archival purposes. Backups are an essential part of a continuity of operations plan as they allow for data protection and recovery.
- Еmail Protection - refers to technology designed to prevent, detect and respond to cyber-attacks delivered through email. The term covers everything from gateways email systems to user behavior to related support services and security tools.
- Password Vault Manager - A password vault, password manager, or password locker is a program that stores usernames and passwords for multiple applications securely and in an encrypted format. Users can access the vault via a single “master” password.
- Vulnerability Assessment & Patch Management - The main difference between patch management and vulnerability management is that patch management is the operational process of applying remediations (patches) to vulnerable systems. Vulnerability management is the process of identifying, scanning, and prioritizing vulnerabilities for remediation.
- Data loss prevention (DLP) - makes sure that users do not send sensitive or critical information outside the corporate network.
- Microsoft Office 365 and Azure Backup and Migration - Microsoft Office 365 is a cloud-based suite of productivity and collaboration tools that includes popular applications such as Word, Excel, PowerPoint, and Outlook. Azure Backup and Migration are cloud-based services offered by Microsoft that allow organizations to protect and migrate their data to the cloud.
- Zero Trust Network Access (ZTNA) Solution - Zero Trust Network Access (ZTNA) is a security model that assumes that every user, device, and network connection is potentially insecure and should not be trusted by default. ZTNA replaces traditional perimeter-based security models, assuming that all network users and devices are trusted.
- Cloud Security - Cloud security is a collection of security measures designed to protect cloud-based infrastructure, applications, and data. These measures ensure user and device authentication, data and resource access control, and data privacy protection.
- Next-Generation Firewall - protects your network by filtering traffic and acting as a guard between your internal network and the rest of the world. Without a Firewall, your business systems could be left wide open and vulnerable to attack. It also serves as another protective layer to block malicious software.
- Active Directory Security and Recovery are critical components of any organization's cybersecurity strategy. Here are some key steps that can be taken to secure and recover Active Directory.
- SIEM & SOAR - SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) are both tools used in cybersecurity to monitor and respond to security threats.
⇒ BOUTIQUE MANAGED SERVICES
- Network domain
- Linux domain
- Microsoft domain
- Virtualization domain
- Database domain
- DevOps-as-a-Service

























