Validato SECURITY CONTROLS VALIDATION PLATFORM
Validate your security controls, continuously
⇒ Who is Validato
Validato is the platform to validate security control effectiveness by using offensive cyber-attack simulations. Validato continuously tests your protection, detection, and ability to respond to cyber incidents. Leading information security analysts and experts are all agreed that the future of enterprise security lies in proactive security, rather than today’s reactive defense. Validato provides a safe and cost-effective way to proactively test and validate your security posture on a regular basis.
Validato gives CISOs and security risk assurance professionals the impartial data that they are looking for in order to answer these questions:
"Are our security controls protecting us as we assume they should be?"
"Are our SOC and Incident Response teams able to detect attacks?"
"How well are we responding to incidents?"
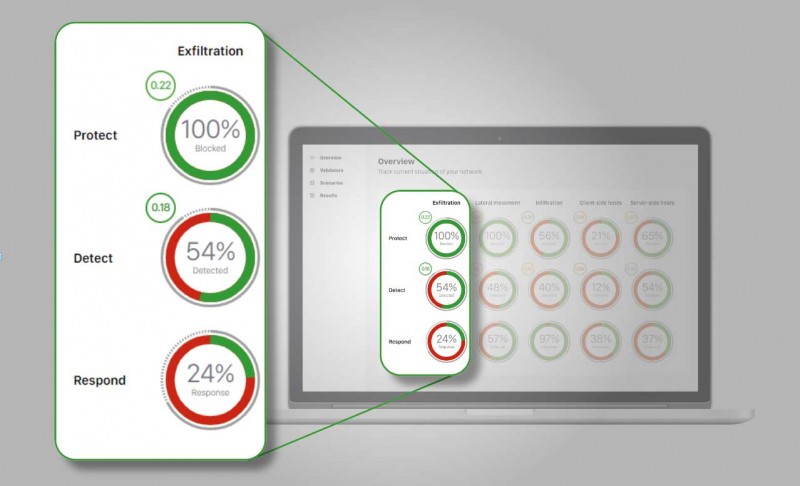
Validato Breach and Attack Simulations can be mapped back to key elements of the NIST CSF framework
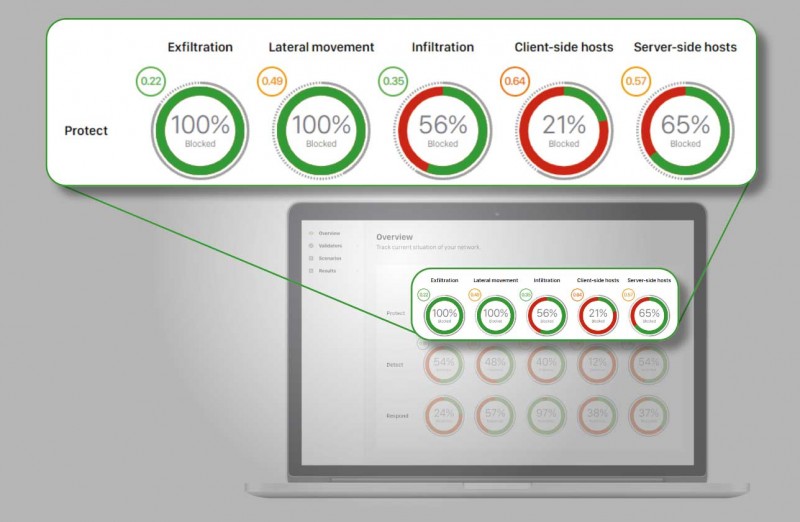
Protect: Are our security controls protecting us from cyber threats?,
Detect: Are our security controls creating events for the Incident Response team to be able to detect attacks?
Respond: Are we responding to and fixing issues in a timely manner?

⇒ How Does Validato Work and How To Set Up
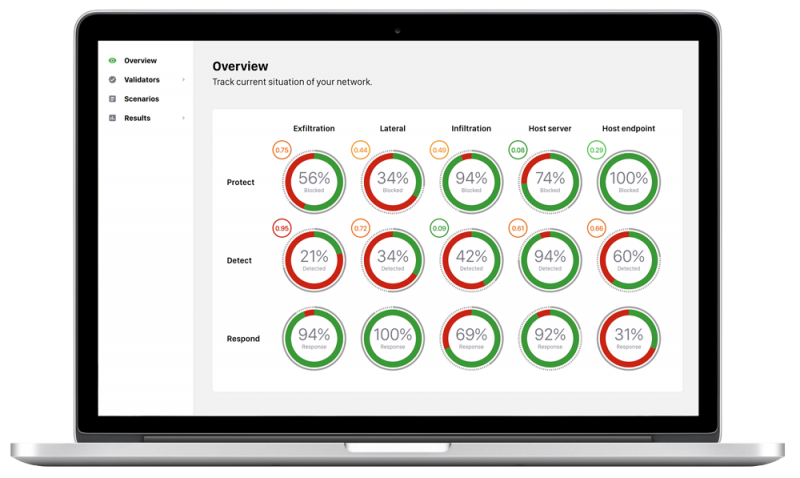
Our team is always happy to elaborate, but simply, the Validato platform runs attack simulations between two or more Validator agents that are deployed on either side of security controls. We measure what simulation attack traffic was sent and what was blocked and/or detected by your security controls.
As a cloud-based service, Validato can be deployed and operational within 30 minutes. Attack simulations are managed by the Validato Management console which communicates securely with Validator agents that are deployed in key nodes of the network.
Here are four simple steps to validate your security controls:
- Deploy - Create and deploy Validator™ simulation agents. Our wizard-based Validator setup process makes Validators effortless to deploy.
- Select - Select your validation test scenario (or run all scenarios). These can be based on threat type, like Ransomware, credential abuse or data exfiltration, threat group … or specific MITRE ATT&CK TTP.
- Validate - Let Validato do its magic. Validato attack simulations run silently in the background with no impact on production environments and can run automatically on a pre-defined schedule, or ad hoc on-demand.
- Analyse - Analyse simulation data and map results back to MITRE ATT&CK™ and SHIELD™. Get immediate insights into how security controls performed and whether security controls detected simulations.

⇒ Platform Features
- Validate your security controls - With Validato you can safely and economically test and validate your security control configurations with a vast range of offensive tactics, techniques, and procedures.
- Understand your resilience & response to a Ransomware attack - Understanding if and how a Ransomware attack could affect your business is a top concern for Boards and security teams alike. Let Validato show you what would happen.
- Understand how a threat actor can gain access to credentials - Think that bad actors cannot gain access to credentials and crown jewel assets? Validato simulates thousands of cyber attack methods to (hopefully) prove you correct.
- Validate your protection, detection & response to cyber threats - Validato does what it says on the tin. It helps Information Security teams to validate their security controls by regularly testing your security control protection, detection, and your team’s response to the attack.
- Map attack simulations to MITRE ATT&CK -Validato mimics and simulates MITRE ATT&CK TTPs to provide a safe, but realistic environment to continuously test your security control configurations and then map back to MITRE ATT&CK and SHIELD.


⇒ Advanced Vision IT Ltd Cybersecurity Products & Software
To build good cybersecurity protection, you need physical products and software that will help strengthen your network against attacks. If you want to view some of the ADVANCED VISION IT's cyber protection solutions, click on the links below.
- Endpoint security and antivirus software - offer a centralized management system from which security administrators can monitor, protect, and investigate vulnerabilities across all endpoints, including computers, mobile devices, servers, and connected devices. Antivirus software helps keep a computer system healthy and free of viruses and other types of malware.
- Employee Monitoring Solution - Employee monitoring solutions are software tools that enable employers to monitor the activities of their employees while they are at work. These solutions can be used to track employees' computer usage, including their internet browsing history, email communication, keystrokes, and application usage.
- Cybersecurity Backup - A backup is a copy of the system or network's data for file restoration or archival purposes. Backups are an essential part of a continuity of operations plan as they allow for data protection and recovery.
- Еmail Protection - refers to technology designed to prevent, detect and respond to cyber-attacks delivered through email. The term covers everything from gateways email systems to user behavior to related support services and security tools.
- Password Vault Manager - A password vault, password manager, or password locker is a program that stores usernames and passwords for multiple applications securely and in an encrypted format. Users can access the vault via a single “master” password.
- Vulnerability Assessment & Patch Management - The main difference between patch management and vulnerability management is that patch management is the operational process of applying remediations (patches) to vulnerable systems. Vulnerability management is the process of identifying, scanning, and prioritizing vulnerabilities for remediation.
- Data loss prevention (DLP) - makes sure that users do not send sensitive or critical information outside the corporate network.
- Cloud Security - Cloud security is a collection of security measures designed to protect cloud-based infrastructure, applications, and data. These measures ensure user and device authentication, data and resource access control, and data privacy protection.
- Next-Generation Firewall - protects your network by filtering traffic and acting as a guard between your internal network and the rest of the world. Without a Firewall, your business systems could be left wide open and vulnerable to attack. It also serves as another protective layer to block malicious software.
- Active Directory Security and Recovery are critical components of any organization's cybersecurity strategy. Here are some key steps that can be taken to secure and recover Active Directory.
- SIEM & SOAR - SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) are both tools used in cybersecurity to monitor and respond to security threats.
⇒ BOUTIQUE MANAGED SERVICES
- Network domain
- Linux domain
- Microsoft domain
- Virtualization domain
- Database domain
- DevOps-as-a-Service
CONTACT OUR TEAM OF PROFESSIONALS FOR A COMPLETELY FREE CONSULTATION
CLAIM YOUR FREE IT AUDIT & CONSULTATION SCHEDULE A CALL WITH OUR TEAM

























