Trellix XDR engine
Stop advanced threats with real-time detection and prevention
that blocks attacks before they strike.

⇒ Who is Trellix
Trellix (formerly FireEye and McAfee Enterprise) is a privately held cybersecurity company founded in 2022. It has been involved in the detection and prevention of major cybersecurity attacks. It provides hardware, software, and services to investigate cybersecurity attacks, protect against malicious software, and analyze IT security risks. Their open and native extended detection and response (XDR) platform helps organizations confronted by today’s most advanced threats gain confidence in the protection and resilience of their operations. Trellix security experts and an extensive partner ecosystem accelerate technology innovation through machine learning and automation to empower over 40,000 business and government customers.
In March 2021, Symphony Technology Group (STG) announced its acquisition of McAfee Enterprise in an all-cash transaction. STG completed the acquisition of McAfee’s Enterprise business in July 2021 with plans for re-branding. In June 2021, FireEye sold its name and products business to STG. STG combined FireEye with its acquisition of McAfee's enterprise business to launch Trellix, an extended detection, and response (XDR) company.
⇒ Trellix XDR Engine
Trellix XDR platform, enabling organizations to realize the benefits of living security and put customers on the path to increased confidence, resilience, security, and success. Here are some main advantages offered by Trellix XDR.
- Comprehensive threat protection - Eliminate blind spots across your security infrastructure by combining the strongest native attack telemetry with the broadest 3rd party threat ingestion – including 4x more integrations of any other security vendor – to provide the most effective and flexible XDR solution available. Trellix correlates threat data from over 1,000 native and open threat sources for expanded threat detection and response, keeping your users, endpoints, and data completely secure.
- Automated Attack Mitigation and Prevention - Trellix XDR Engine learns and adapts at the speed of threat actors, delivering immediate insights about the evolving attack landscape to help you stay ahead of the latest threats.
- Streamlined SOC Experience - Enrich and accelerate threat investigations with simplified threat landscape views and guided response workflows that reduce the manual strain on overloaded security operations teams. Trellix XDR Engine identifies and prioritizes critical alerts, providing SOC teams with the ability to easily identify and rapidly stop multi-vector attacks.
- Actionable threat intelligence - Gain real-time adversarial insights with threat intelligence gleaned from over 40,000 organizations around the world. Trellix XDR Engine leverages industry-leading threat intelligence, which provides the ability to respond to current threats in real-time, while adjusting for approaching threats and preventing future attacks.
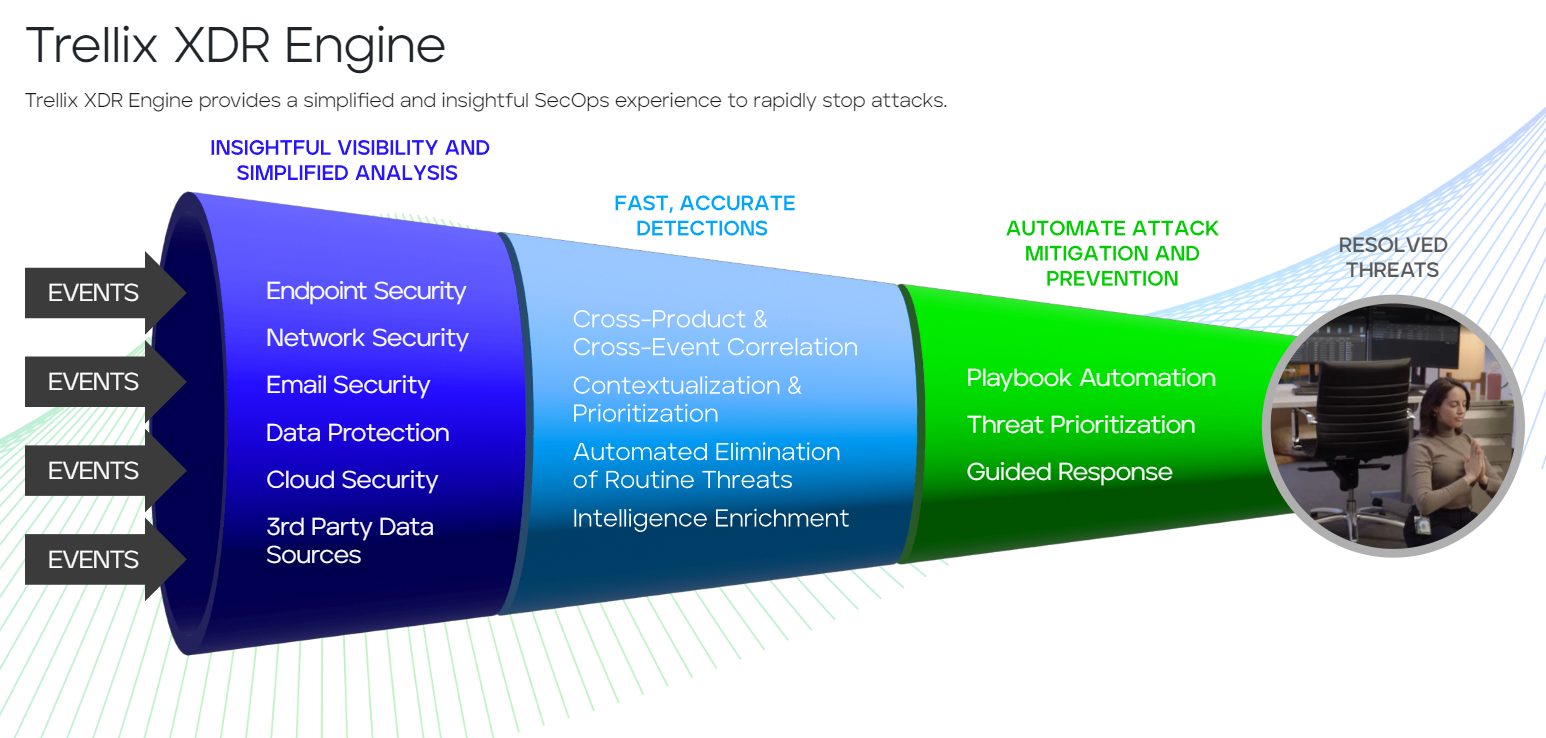
⇒ Тrellix XDR Key Benefits
- Reduces cyber risks - By providing improved visibility across the threat landscapes coupled with industry-leading threat detection technology, Trellix XDR stops cyberattacks before they happen.
- Optimizes SOC resources - Addressing today’s scrutinized security budgets and the scarcity of experienced security talent, Trellix XDR identifies and prioritizes critical alerts and provides automated guidance and responses for mitigating attacks, reducing the manual strain on SOC teams.
- Simplifies SOC operations - Detect and prioritize emerging high-impact threats leveraging real-time, automation security analytics and accelerate threat investigations with an intuitive, directed solution built for security analysts by security analysts.
- Reduces SOC costs - SOC costs have exploded with the proliferation of disconnected, ineffective security tools, each with its acquisition, operations, and maintenance costs, not to mention staff.

⇒ Advanced Vision IT Ltd Cybersecurity Products & Software
To build good cybersecurity protection, you need physical products and software that will help strengthen your network against attacks. If you want to view some of the ADVANCED VISION IT's cyber protection solutions, click on the links below.
- Endpoint security and antivirus software - offer a centralized management system from which security administrators can monitor, protect, and investigate vulnerabilities across all endpoints, including computers, mobile devices, servers, and connected devices. Antivirus software helps keep a computer system healthy and free of viruses and other types of malware.
- Employee Monitoring Solution - Employee monitoring solutions are software tools that enable employers to monitor the activities of their employees while they are at work. These solutions can be used to track employees' computer usage, including their internet browsing history, email communication, keystrokes, and application usage.
- Cybersecurity Backup - A backup is a copy of the system or network's data for file restoration or archival purposes. Backups are an essential part of a continuity of operations plan as they allow for data protection and recovery.
- Еmail Protection - refers to technology designed to prevent, detect and respond to cyber-attacks delivered through email. The term covers everything from gateways email systems to user behavior to related support services and security tools.
- Password Vault Manager - A password vault, password manager, or password locker is a program that stores usernames and passwords for multiple applications securely and in an encrypted format. Users can access the vault via a single “master” password.
- Vulnerability Assessment & Patch Management - The main difference between patch management and vulnerability management is that patch management is the operational process of applying remediations (patches) to vulnerable systems. Vulnerability management is the process of identifying, scanning, and prioritizing vulnerabilities for remediation.
- Data loss prevention (DLP) - makes sure that users do not send sensitive or critical information outside the corporate network.
- Cloud Security - Cloud security is a collection of security measures designed to protect cloud-based infrastructure, applications, and data. These measures ensure user and device authentication, data and resource access control, and data privacy protection.
- Next-Generation Firewall - protects your network by filtering traffic and acting as a guard between your internal network and the rest of the world. Without a Firewall, your business systems could be left wide open and vulnerable to attack. It also serves as another protective layer to block malicious software.
- Active Directory Security and Recovery are critical components of any organization's cybersecurity strategy. Here are some key steps that can be taken to secure and recover Active Directory.
- SIEM & SOAR - SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) are both tools used in cybersecurity to monitor and respond to security threats.
⇒ BOUTIQUE MANAGED SERVICES
- Network domain
- Linux domain
- Microsoft domain
- Virtualization domain
- Database domain
- DevOps-as-a-Service
CONTACT OUR TEAM OF PROFESSIONALS FOR A COMPLETELY FREE CONSULTATION
CLAIM YOUR FREE IT AUDIT & CONSULTATION SCHEDULE A CALL WITH OUR TEAM

























