QUEST CHANGE AUDITOR FOR ACTIVE DIRECTORY

⇒ What is Quest Change Auditor?
- Quest Change Auditor is a security solution designed to help organizations track and audit changes made to critical systems, applications, and data. It provides real-time alerts, reports, and analysis of user activity to help identify and respond to suspicious behavior.
- Change Auditor can be used to audit a wide range of systems and applications, including Microsoft Active Directory, Exchange, SharePoint, SQL Server, and Office 365. It provides detailed tracking and auditing of changes made to these systems, including who made the changes, when they were made, and what was changed.
- The solution also includes advanced analytics and threat detection capabilities, such as machine learning and behavior-based analysis, to help identify anomalous activity and potential security threats. Change Auditor can be integrated with SIEM systems, threat intelligence feeds, and other security tools to provide a comprehensive security solution.
- Overall, Quest Change Auditor helps organizations improve their security posture by providing real-time visibility into user activity, reducing the time it takes to detect and respond to security incidents, and enabling organizations to quickly investigate and remediate potential security threats.
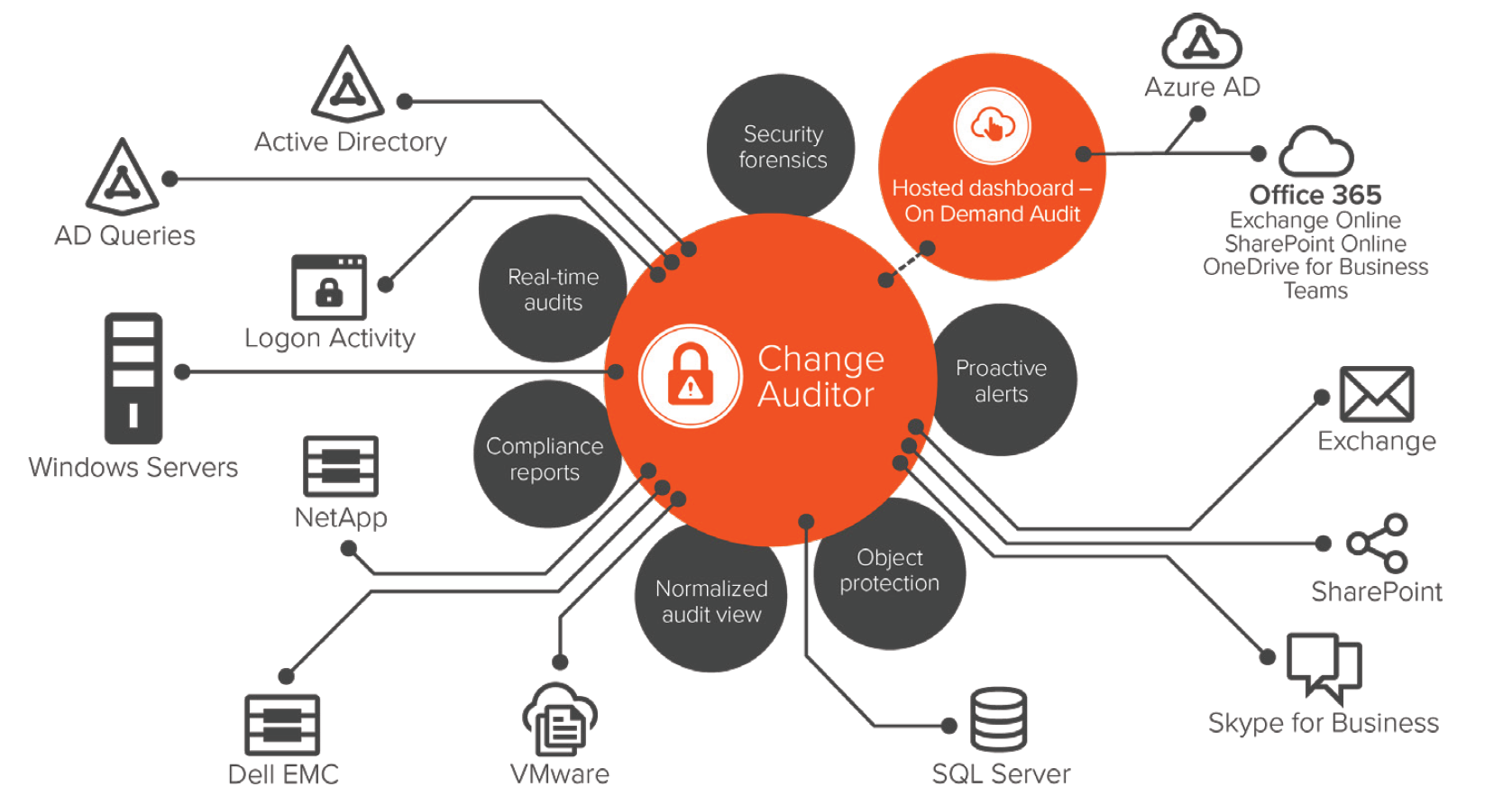
⇒ Quest Change Auditor Key Features
- Security threat monitoring - Detect attack attempts, lateral movement through your network, and post-attack damage done to your critical workloads like Exchange and file systems.
- Complete coverage - Detect indicators of compromise (IOCs) across AD and Azure AD to catch attacks before they start, and audit suspicious user activity across file servers, Office 365 and Exchange to monitor adversaries already in the network.
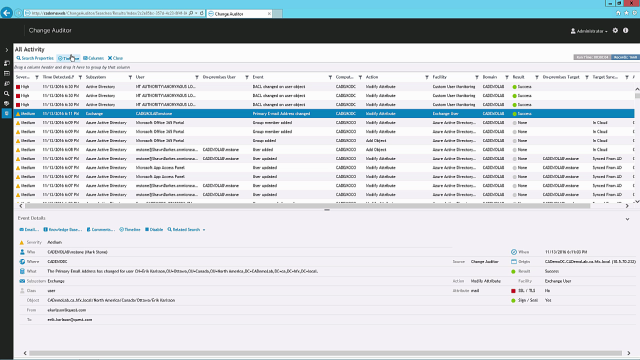
- Threat timelines - View, highlight and filter change events and discover their relation to other security events in chronological order across your Microsoft environment for better forensic analysis and security incident response.
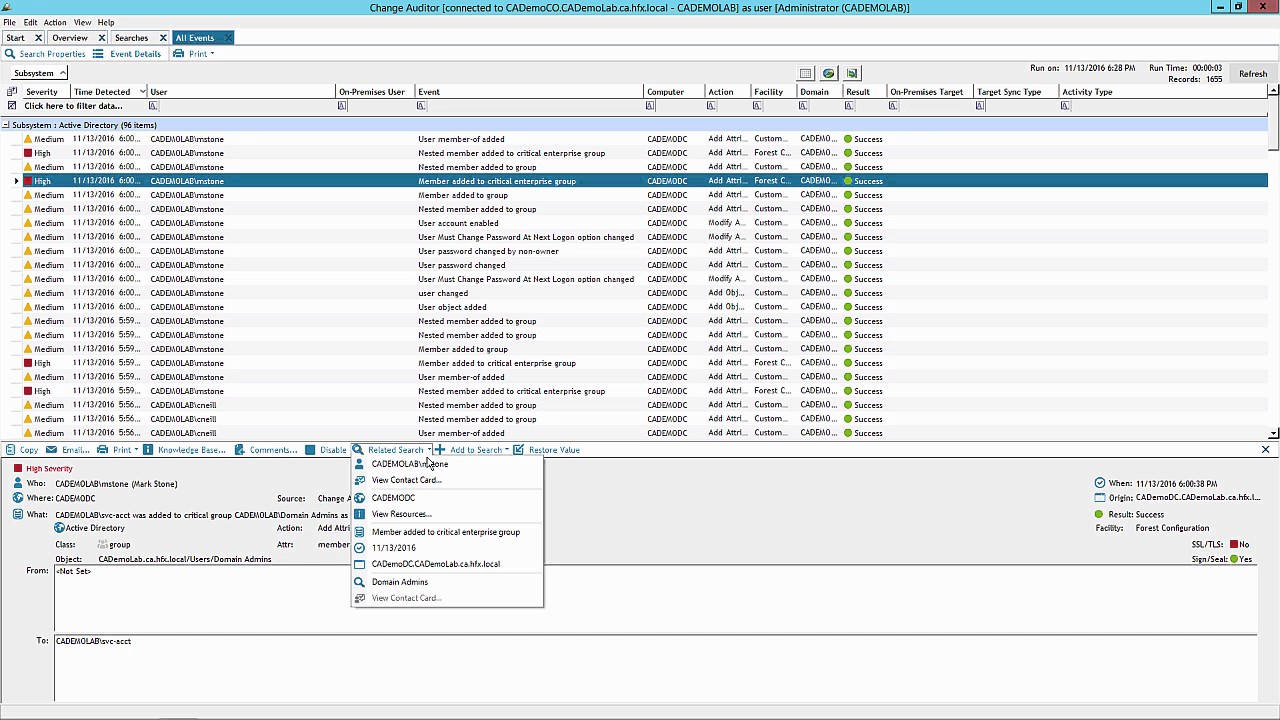
- Related searches - Provide instant, one-click access to all information on the change you're viewing and all related events, such as what other changes came from specific users and workstations, eliminating guesswork and unknown security concerns.
- Superior auditing engine - Remove auditing limitations and capture change information without the need for system-provided audit logs, eliminating blind spots, and resulting in increased visibility of suspicious user activity.
- Secure AD attack paths - Identify Tier Zero assets and the attack paths to them using BloodHound Enterprise and monitor and secure those attack paths to avoid exploits with Change Auditor.
- SIEM integration - Enrich SIEM solutions including Sentinel, Splunk, ArcSight, QRadar or any platform supporting Syslog by integrating Change Auditor’s detailed activity logs.
- Auditor-ready reporting - Generate comprehensive reports to support regulatory compliance mandates for GDPR, PCI DSS, HIPAA, SOX, FISMA / NIST, GLBA and more.
⇒ Quest Change Auditor Platforms
- Active Directory - Change Auditor for Active Directory and Change Auditor for Logon Activity detect and alert on changes to critical objects in Microsoft Active Directory and Azure AD with a single, correlated view across your hybrid AD environment. Track Kerberos, NTLM and ADFS authentications to identify vulnerabilities and exploits.
- Azure AD and Office 365 - With just a few clicks, you can pair Change Auditor and On Demand Audit to get a single, hosted view of all changes made across AD, Azure AD, Exchange Online, SharePoint Online, OneDrive for Business and Teams.
- Windows Server - Change Auditor for Windows File Servers helps you control and audit changes to Microsoft Windows Server efficiently and cost-effectively. Proactively track, audit, report on and alerts on vital changes, including user and administrator accounts, in real time and without the overhead of system-provided auditing.
- Exchange - Change Auditor for Exchange simplifies the Exchange auditing process. Track, audit, report and alert on Microsoft Exchange on-premises and Exchange Online changes in real time within a single, correlated view.
- SQL Server - Change Auditor for SQL Server makes database auditing of Microsoft SQL Server easy and secure. It tracks, audits, reports on and alerts on changes in real time, translating events into simple terms and eliminating the time and complexity required for auditing.
- Network-attached storage - Ensure the security, compliance and control of files, folders and shares by tracking, auditing, reporting and alerting on all changes in real time. With Change Auditor for NetApp and Change Auditor for EMC, you can report on and analyze events and changes without the complexity and time required with built-in auditing functions.
⇒ Quest Change Auditor Use Cases
- Compliance and Security Auditing: Change Auditor helps organizations comply with industry regulations such as HIPAA, SOX, GDPR, and PCI-DSS by providing detailed reporting on changes made in the IT environment. It can track changes made to Active Directory, Exchange, SharePoint, and other critical systems, alerting administrators to any suspicious activity that could indicate a security breach.
- Troubleshooting and Root Cause Analysis: Change Auditor provides detailed information about changes made to IT systems, allowing administrators to quickly identify and resolve issues. It provides real-time visibility into changes made to systems, including who made the change, what change was made, and when the change occurred.
- Change Management: Change Auditor provides a centralized platform for managing and approving changes made to IT systems. It allows administrators to create workflows and approvals for changes, ensuring that changes are properly tested and documented before they are implemented.
- Privileged User Monitoring: Change Auditor can track and monitor the activity of privileged users such as administrators, helping to ensure that they are not abusing their access privileges. It provides detailed reporting on the activity of privileged users, alerting administrators to any suspicious activity.
- Data Governance: Change Auditor provides visibility into changes made to sensitive data, helping organizations maintain compliance with data privacy regulations. It can track changes made to files and folders, including who made the change, what change was made, and when the change occurred.

⇒ Advanced Vision IT Ltd Cybersecurity Products & Software
To build good cybersecurity protection, you need physical products and software that will help strengthen your network against attacks. If you want to view some of the ADVANCED VISION IT's cyber protection solutions, click on the links below.
- Endpoint security and antivirus software - offer a centralized management system from which security administrators can monitor, protect, and investigate vulnerabilities across all endpoints, including computers, mobile devices, servers, and connected devices. Antivirus software helps keep a computer system healthy and free of viruses and other types of malware.
- Employee Monitoring Solution - Employee monitoring solutions are software tools that enable employers to monitor the activities of their employees while they are at work. These solutions can be used to track employees' computer usage, including their internet browsing history, email communication, keystrokes, and application usage.
- Cybersecurity Backup - A backup is a copy of the system or network's data for file restoration or archival purposes. Backups are an essential part of a continuity of operations plan as they allow for data protection and recovery.
- Еmail Protection - refers to technology designed to prevent, detect and respond to cyber-attacks delivered through email. The term covers everything from gateways email systems to user behavior to related support services and security tools.
- Password Vault Manager - A password vault, password manager, or password locker is a program that stores usernames and passwords for multiple applications securely and in an encrypted format. Users can access the vault via a single “master” password.
- Vulnerability Assessment & Patch Management - The main difference between patch management and vulnerability management is that patch management is the operational process of applying remediations (patches) to vulnerable systems. Vulnerability management is the process of identifying, scanning, and prioritizing vulnerabilities for remediation.
- Data loss prevention (DLP) - makes sure that users do not send sensitive or critical information outside the corporate network.
- Microsoft Office 365 and Azure Backup and Migration - Microsoft Office 365 is a cloud-based suite of productivity and collaboration tools that includes popular applications such as Word, Excel, PowerPoint, and Outlook. Azure Backup and Migration are cloud-based services offered by Microsoft that allow organizations to protect and migrate their data to the cloud.
- Zero Trust Network Access (ZTNA) Solution - Zero Trust Network Access (ZTNA) is a security model that assumes that every user, device, and network connection is potentially insecure and should not be trusted by default. ZTNA replaces traditional perimeter-based security models, assuming that all network users and devices are trusted.
- Cloud Security - Cloud security is a collection of security measures designed to protect cloud-based infrastructure, applications, and data. These measures ensure user and device authentication, data and resource access control, and data privacy protection.
- Next-Generation Firewall - protects your network by filtering traffic and acting as a guard between your internal network and the rest of the world. Without a Firewall, your business systems could be left wide open and vulnerable to attack. It also serves as another protective layer to block malicious software.
- Active Directory Security and Recovery are critical components of any organization's cybersecurity strategy. Here are some key steps that can be taken to secure and recover Active Directory.
- SIEM & SOAR - SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) are both tools used in cybersecurity to monitor and respond to security threats.
⇒ BOUTIQUE MANAGED SERVICES
- Network domain
- Linux domain
- Microsoft domain
- Virtualization domain
- Database domain
- DevOps-as-a-Service
CONTACT OUR TEAM OF PROFESSIONALS FOR A COMPLETELY FREE CONSULTATION
CLAIM YOUR FREE IT AUDIT & CONSULTATION SCHEDULE A CALL WITH OUR TEAM

























