TENABLE LUMIN
How Secure is the Business? Calculate and Compare Your Cyber Risk with Tenable Lumin.
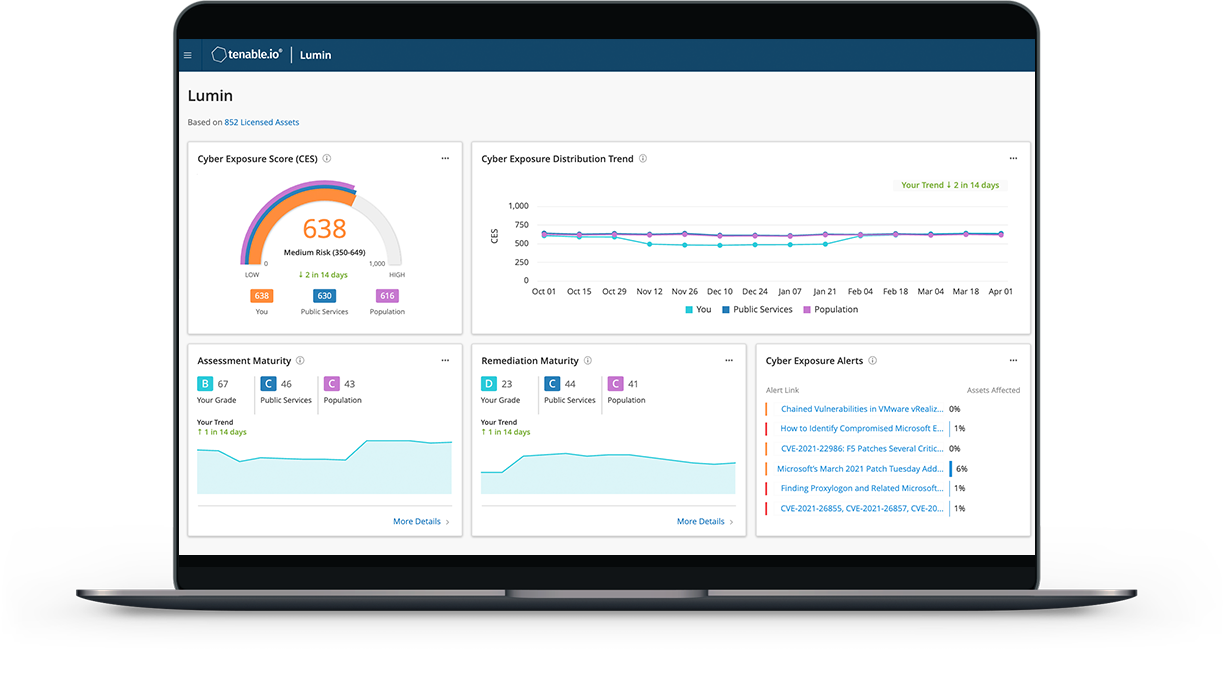
⇒ What is Tenable Lumin?
- Tenable Lumin enables organizations to effectively measure their Cyber Exposure and benchmark their performance internally against different groups and externally against industry peers. To accomplish this, Tenable combines data about the real-world threat vulnerabilities pose with asset criticality context to calculate a Cyber Exposure Score, transforming raw technical data into business insights.
- Tenable Lumin helps organizations elevate cyber risk to that of other risk management disciplines through accurate and actionable measurement of cyber exposure, both within the organization and against peer organizations.
- Tenable Lumin helps security teams move from arcane technical language to a concise language suitable for business decision-making by translating technical data into business insights.
- These insights help security teams prioritize and focus remediation based on business risk and receive guidance on the optimal remediation actions to take for better collaboration with IT.


⇒ How Does The Tenable Lumin Find Assets and Vulnerabilities?
- Tenable Lumin combines several data sources, such as vulnerability data, threat intelligence and asset criticality, to help security leaders quantify cyber risk and maximize cyber risk mitigation. Tenable Exposure.ai technology leverages the industry's most extensive vulnerability intelligence and one of the industry's largest data science organizations, allowing us to provide comprehensive benchmarking capabilities to compare your cyber risk to peers and algorithms for machine learning to provide accurate cyber risk calculations.
- Calculate - Advanced analysis and risk-based exposure scoring weighs asset value and criticality, vulnerabilities, threat context and security program effectiveness – providing clear guidance about what to focus on.
- Communicate - Visualizations of the entire attack surface allow anyone – from analysts to executives – to quickly understand and communicate your organization’s Cyber Exposure.
- Compare - Exposure quantification and benchmarking allow you to compare your effectiveness for internal operations and against peers. Identify areas of focus and optimize security investments.
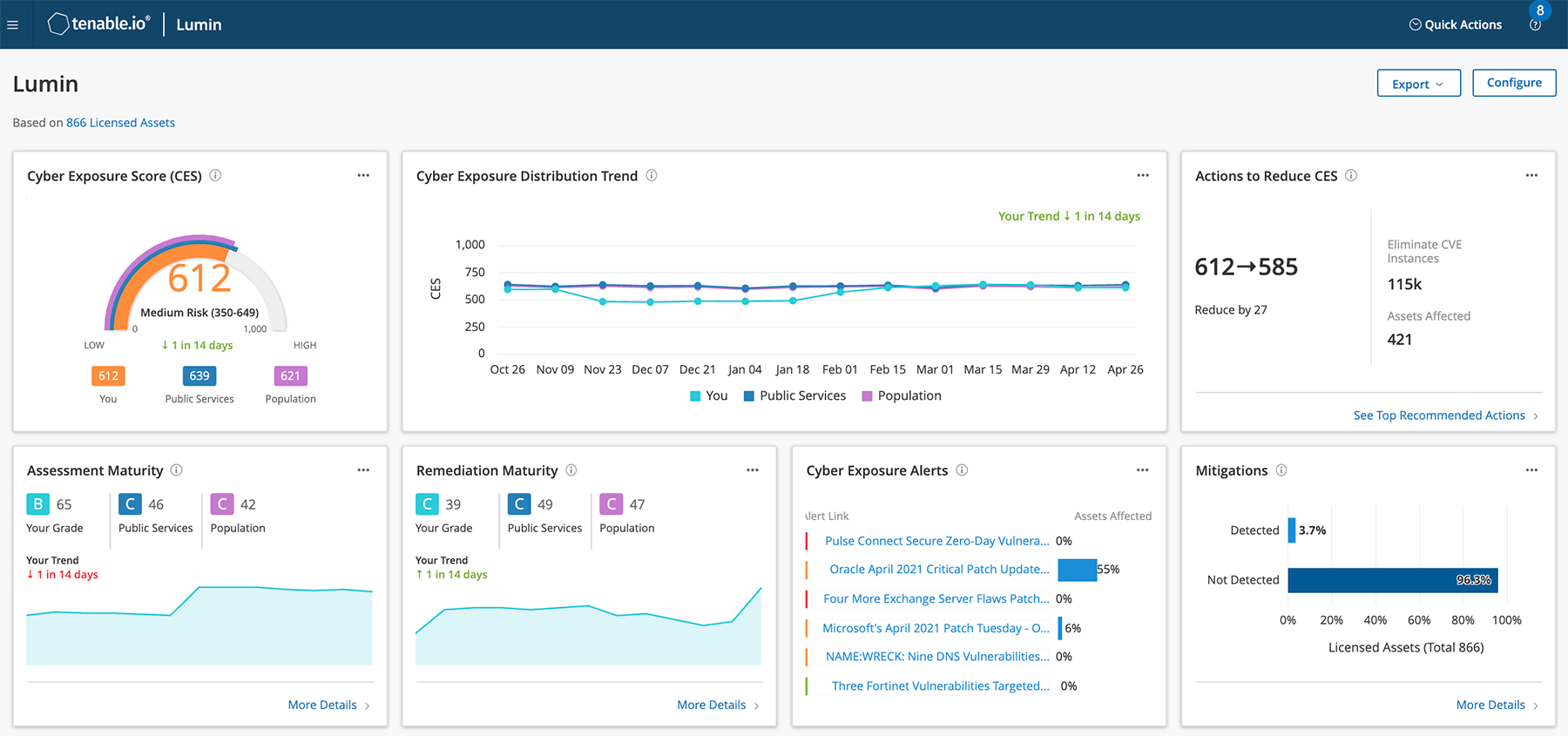
⇒ Gain Business Insights Into Your Organization's Overall Cyber Risk
- Risk-Based Exposure Scoring and Prioritization - Advanced risk-based Cyber Exposure analysis and scoring weigh vulnerabilities, threat data, and asset criticality along with remediation and assessment maturity. Provides clear guidance on where to focus remediation efforts.
- Unified View of Assets and Vulnerabilities - Gain insights through a single, comprehensive view of your entire attack surface (including traditional IT, public and private clouds, web applications and containers and IoT and OT).
- Deep Business Insights - See how your organization’s cyber risk changes over time. Manage risk based on quantifiable metrics aligned to the business. Quickly determine the actions you need to take to reduce your cyber exposure.
- Exposure Analytics, Benchmarking and Decision Support - Track cyber risk reduction over time and compare your cybersecurity effectiveness within your organization and to industry peers. Insight into your exposure to new critical vulnerabilities.
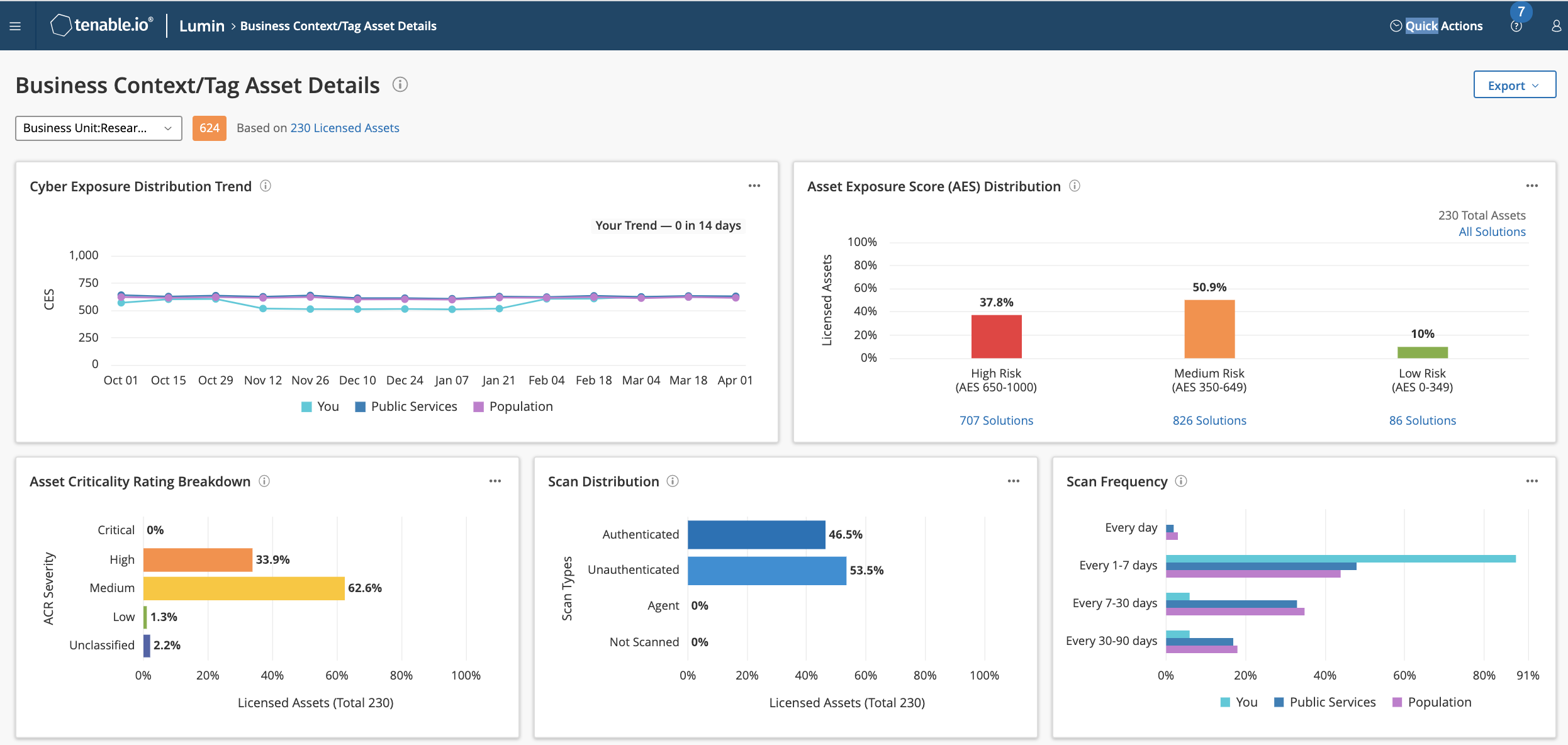
⇒ View Business Context for Cyber Exposure Reduction Efforts
- Risk-Based Exposure Scoring and Prioritization - Detailed analysis of exposure scores for individual assets and recommended remediation solutions.
- Deep Insight Into Your Entire Attack Surface - Machine learning predicts the potential risk of assets that have yet to receive an in-depth assessment.
- Program Effectiveness Measurements - Insight and perspective into your security processes. Measure and benchmark your assessment and remediation maturity. Quantify how well you scan your environment and your effectiveness in remediating vulnerabilities.

⇒ Advanced Vision IT Ltd Cybersecurity Products & Software
To build good cybersecurity protection, you need physical products and software that will help strengthen your network against attacks. If you want to view some of the ADVANCED VISION IT's cyber protection solutions, click on the links below.
- Endpoint security and antivirus software - offer a centralized management system from which security administrators can monitor, protect, and investigate vulnerabilities across all endpoints, including computers, mobile devices, servers, and connected devices. Antivirus software helps keep a computer system healthy and free of viruses and other types of malware.
- Employee Monitoring Solution - Employee monitoring solutions are software tools that enable employers to monitor the activities of their employees while they are at work. These solutions can be used to track employees' computer usage, including their internet browsing history, email communication, keystrokes, and application usage.
- Cybersecurity Backup - A backup is a copy of the system or network's data for file restoration or archival purposes. Backups are an essential part of a continuity of operations plan as they allow for data protection and recovery.
- Еmail Protection - refers to technology designed to prevent, detect and respond to cyber-attacks delivered through email. The term covers everything from gateways email systems to user behavior to related support services and security tools.
- Password Vault Manager - A password vault, password manager, or password locker is a program that stores usernames and passwords for multiple applications securely and in an encrypted format. Users can access the vault via a single “master” password.
- Vulnerability Assessment & Patch Management - The main difference between patch management and vulnerability management is that patch management is the operational process of applying remediations (patches) to vulnerable systems. Vulnerability management is the process of identifying, scanning, and prioritizing vulnerabilities for remediation.
- Data loss prevention (DLP) - makes sure that users do not send sensitive or critical information outside the corporate network.
- Microsoft Office 365 and Azure Backup and Migration - Microsoft Office 365 is a cloud-based suite of productivity and collaboration tools that includes popular applications such as Word, Excel, PowerPoint, and Outlook. Azure Backup and Migration are cloud-based services offered by Microsoft that allow organizations to protect and migrate their data to the cloud.
- Zero Trust Network Access (ZTNA) Solution - Zero Trust Network Access (ZTNA) is a security model that assumes that every user, device, and network connection is potentially insecure and should not be trusted by default. ZTNA replaces traditional perimeter-based security models, assuming that all network users and devices are trusted.
- Cloud Security - Cloud security is a collection of security measures designed to protect cloud-based infrastructure, applications, and data. These measures ensure user and device authentication, data and resource access control, and data privacy protection.
- Next-Generation Firewall - protects your network by filtering traffic and acting as a guard between your internal network and the rest of the world. Without a Firewall, your business systems could be left wide open and vulnerable to attack. It also serves as another protective layer to block malicious software.
- Active Directory Security and Recovery are critical components of any organization's cybersecurity strategy. Here are some key steps that can be taken to secure and recover Active Directory.
- SIEM & SOAR - SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) are both tools used in cybersecurity to monitor and respond to security threats.
⇒ BOUTIQUE MANAGED SERVICES
- Network domain
- Linux domain
- Microsoft domain
- Virtualization domain
- Database domain
- DevOps-as-a-Service

























