SIEM & SOAR MANAGED SERVICES WITH LOGPOINT
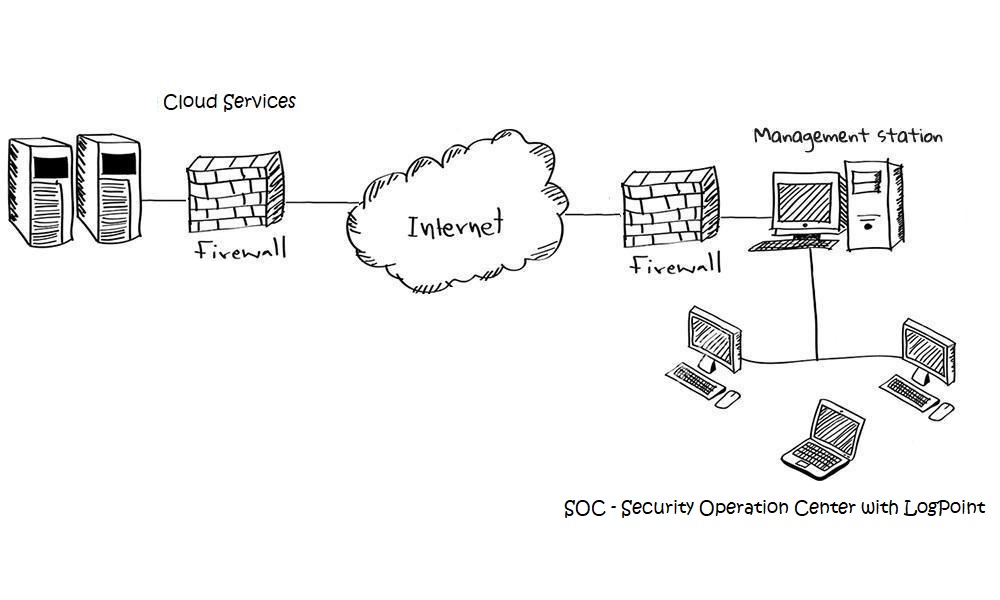
- LOGPOINT SIEM&SOAR INITIAL INSTALL: Initial planning and installation of new services and applications.
- LOGPOINT CLOUD AND ON-PREMISE PROVISIONING STRATEGY: Logpoint strategy for organizations and choosing the best solution for your needs.
- LOGPOINT UEBA INTEGRATION : Guidance in implementing UEBA - User and Entity Behavior Analytics.
- LOGPOINT SIEM/SOAR ADMINISTRATION: Systems management, Daily Support, Monitoring and Security Analysis(SOC).

Named Account Manager
for any business and Project related questions

Cybersecurity Systems Integration Engineers

Named Service Manager

Professional Services
for any business and Project related questions
Architecture advisors

Managed Monitoring and Incident Response

Integrations of Security Products

Security Advisors
⇒ About Logpoint
Logpoint is committed to creating the best SIEM in the world. Logpoint enable organizations to convert data into actionable intelligence: supporting cybersecurity, compliance, network operations, and business decisions. Logpoint’s advanced next-gen SIEM and UEBA solutions provides analytics and automation capabilities that enable their customers to securely build, manage and effectively transform their businesses.
- Logpoint provides cybersecurity solutions that protect the digital heart of organizations.
- Logpoint creates software that augments security teams to make confident decisions, feel justified in their choices, and be more efficient when protecting organizations.
- That principle has earned the trust of more than a thousand organizations worldwide.
- SIEM and UEBA solution is second to none when bolstering security teams in the fight against the ever-evolving threat landscape.

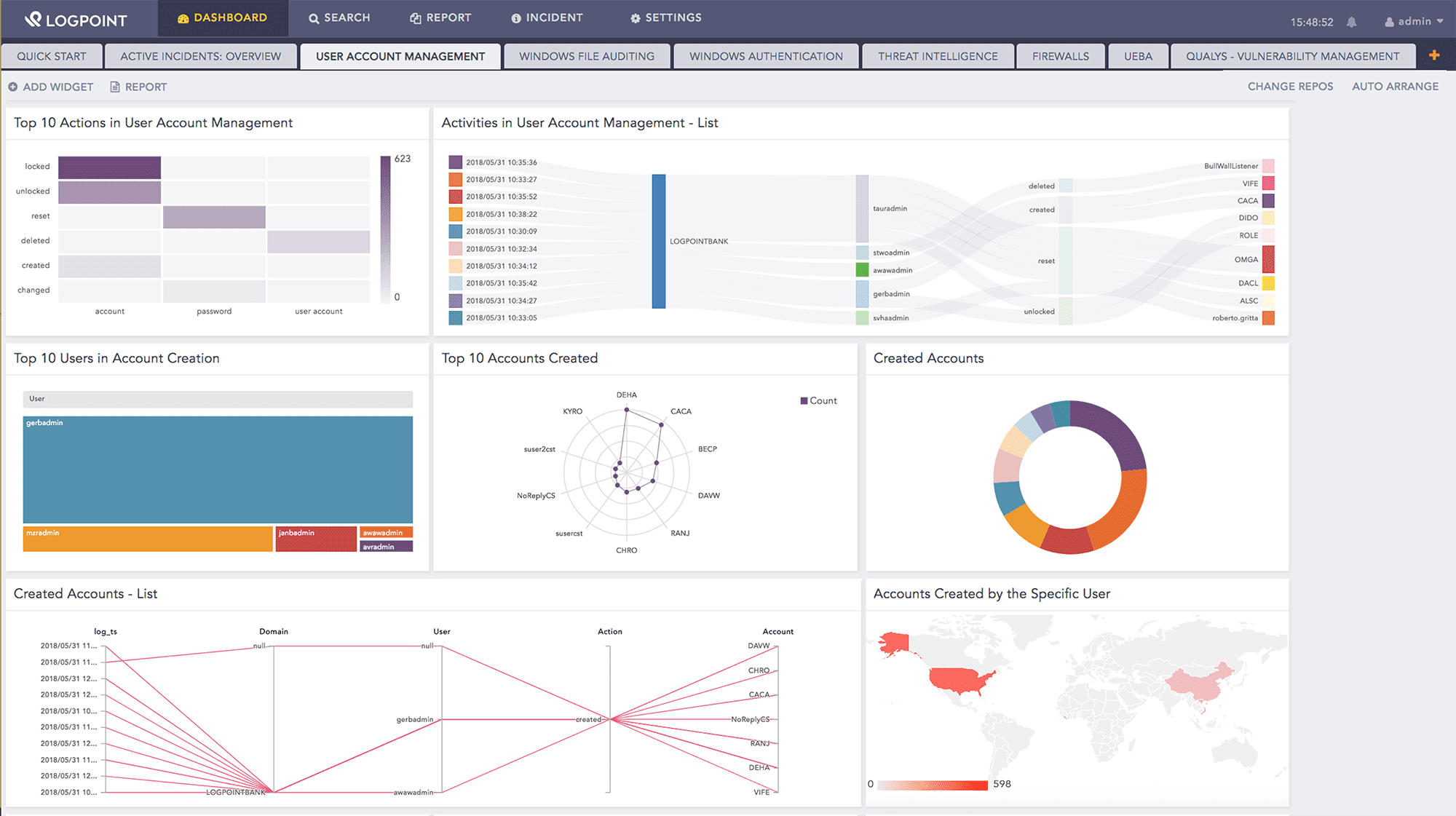
⇒ About Logpoint SIEM
- Security information and event management (SIEM) is a tool that provides monitoring, detection, and alerting of security events or incidents within an IT environment. It provides a comprehensive and centralized view of the security posture of an IT infrastructure and gives enterprise security professionals insight into the activities within their IT environment.
- SIEM software collects and aggregates log data generated throughout the organization's technology infrastructure, from host systems and applications to network and security devices, such as firewalls and antivirus. The software then identifies, categorizes and analyzes incidents and events. The SIEM analysis delivers real-time alerts, dashboards, or reports to several critical business and management units.
Logpoint SIEM Business Use Cases
|

⇒ About Logpoint UEBA
- LogPoint UEBA, short for Logpoint User and Entity Behavior Analytics, is a security solution that helps you detect cyberattacks before they become a threat to your organization. It helps you manage potential breaches efficiently and provides the tools to analyze the detected anomalies.
- Utilizing unsupervised machine learning, LogPoint UEBA observes the behavior of each user and entity in the network to build baselines for normal behavior, and actions are then evaluated against these baselines. To set a proper baseline, UEBA requires a minimum of 30 days of historical data.
Logpoint UEBA Business Use Cases
|
⇒ Why Choose Logpoint?
- Logpoint's feedback from the business - Customers continuously rate Logpoint support and services with 98% satisfaction.
- Logpoint offers a unified security operations platform - Logpoint facilitates customers with a single platform at the heart of their security organization. This increases automation capabilities and enables security teams to efficient responses to threats.
- Avoid surprise costs with predictable licensing - Logpoint licensing is based on the number of nodes (e.g., Laptops or Servers ) sending logs to the platform. Customers can have peace of mind that their budget will not increase alongside data volume.

⇒ Advanced Vision IT Ltd Cybersecurity Products & Software
To build good cybersecurity protection, you need physical products and software that will help strengthen your network against attacks. If you want to view some of the ADVANCED VISION IT's cyber protection solutions, click on the links below.
- Endpoint security and antivirus software - offer a centralized management system from which security administrators can monitor, protect, and investigate vulnerabilities across all endpoints, including computers, mobile devices, servers, and connected devices. Antivirus software helps keep a computer system healthy and free of viruses and other types of malware.
- Employee Monitoring Solution - Employee monitoring solutions are software tools that enable employers to monitor the activities of their employees while they are at work. These solutions can be used to track employees' computer usage, including their internet browsing history, email communication, keystrokes, and application usage.
- Cybersecurity Backup - A backup is a copy of the system or network's data for file restoration or archival purposes. Backups are an essential part of a continuity of operations plan as they allow for data protection and recovery.
- Еmail Protection - refers to technology designed to prevent, detect and respond to cyber-attacks delivered through email. The term covers everything from gateways email systems to user behavior to related support services and security tools.
- Password Vault Manager - A password vault, password manager, or password locker is a program that stores usernames and passwords for multiple applications securely and in an encrypted format. Users can access the vault via a single “master” password.
- Vulnerability Assessment & Patch Management - The main difference between patch management and vulnerability management is that patch management is the operational process of applying remediations (patches) to vulnerable systems. Vulnerability management is the process of identifying, scanning, and prioritizing vulnerabilities for remediation.
- Data loss prevention (DLP) - makes sure that users do not send sensitive or critical information outside the corporate network.
- Microsoft Office 365 and Azure Backup and Migration - Microsoft Office 365 is a cloud-based suite of productivity and collaboration tools that includes popular applications such as Word, Excel, PowerPoint, and Outlook. Azure Backup and Migration are cloud-based services offered by Microsoft that allow organizations to protect and migrate their data to the cloud.
- Zero Trust Network Access (ZTNA) Solution - Zero Trust Network Access (ZTNA) is a security model that assumes that every user, device, and network connection is potentially insecure and should not be trusted by default. ZTNA replaces traditional perimeter-based security models, assuming that all network users and devices are trusted.
- Cloud Security - Cloud security is a collection of security measures designed to protect cloud-based infrastructure, applications, and data. These measures ensure user and device authentication, data and resource access control, and data privacy protection.
- Next-Generation Firewall - protects your network by filtering traffic and acting as a guard between your internal network and the rest of the world. Without a Firewall, your business systems could be left wide open and vulnerable to attack. It also serves as another protective layer to block malicious software.
- Active Directory Security and Recovery are critical components of any organization's cybersecurity strategy. Here are some key steps that can be taken to secure and recover Active Directory.
- SIEM & SOAR - SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) are both tools used in cybersecurity to monitor and respond to security threats.
⇒ BOUTIQUE MANAGED SERVICES
- Network domain
- Linux domain
- Microsoft domain
- Virtualization domain
- Database domain
- DevOps-as-a-Service

























