Logpoint software as a service
⇒ What is Logpoint Software-as-a-Service (SaaS)?
LogPoint is a security information and event management (SIEM) solution that provides real-time monitoring, analysis, and reporting of security events across an organization's entire IT infrastructure. LogPoint's SaaS (Software-as-a-Service) offering provides a cloud-based solution for organizations to implement SIEM without the need for on-premises hardware or software.
LogPoint's SaaS solution offers several benefits, including:
- Scalability: LogPoint's SaaS solution can scale up or down based on an organization's needs, making it suitable for organizations of all sizes.
- Ease of deployment: LogPoint's SaaS solution can be deployed quickly and easily without the need for on-premises hardware or software, reducing deployment time and costs.
- Flexibility: LogPoint's SaaS solution can be customized to meet an organization's specific needs, allowing for a tailored solution that meets their unique requirements.
- Real-time monitoring: LogPoint's SaaS solution provides real-time monitoring and analysis of security events, allowing organizations to quickly detect and respond to threats.
LogPoint's SaaS solution includes features such as threat intelligence, compliance management, incident response, and reporting. The solution is designed to help organizations improve their security posture and reduce the risk of data breaches and other security incidents.

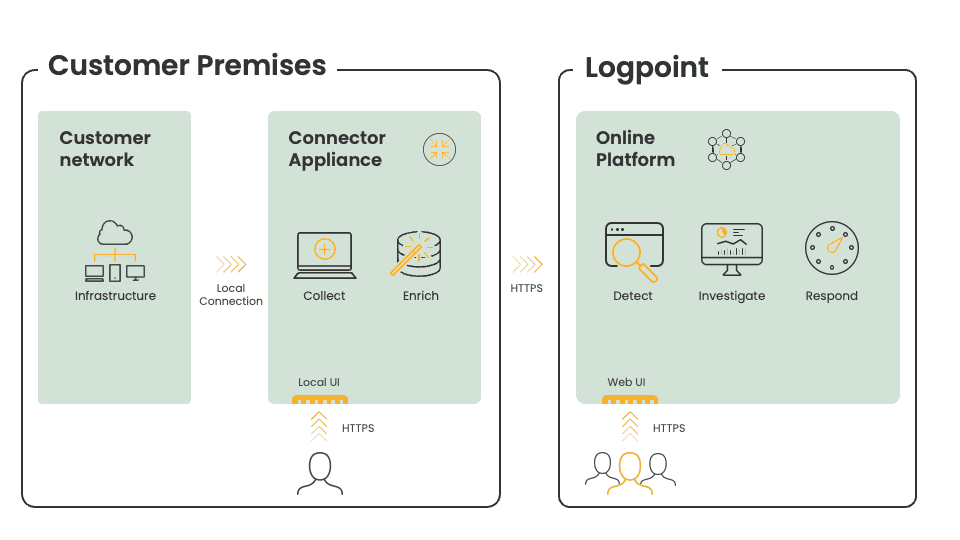
⇒ How it work?
LogPoint SaaS is a cloud-based security information and event management (SIEM) solution that provides a centralized platform for collecting, analyzing, and responding to security events across an organization's IT infrastructure.
Here is how LogPoint SaaS works:
- Data Collection: LogPoint SaaS collects security data from various sources, such as endpoints, network devices, and cloud environments. It supports a wide range of log sources, including Windows and Linux systems, firewalls, intrusion detection systems (IDS), and other security tools.
- Data Processing and Analysis: The collected data is then processed and analyzed using LogPoint's machine learning algorithms and correlation rules to identify potential security threats. The platform provides real-time monitoring and alerting, as well as historical analysis and reporting.
- Incident Response: When a security incident is detected, LogPoint SaaS provides tools for incident response and remediation. This includes workflow automation, ticketing and case management, and integrations with third-party security tools.
- Compliance Reporting: LogPoint SaaS provides a range of compliance reporting capabilities, including support for regulatory standards such as PCI DSS, GDPR, and HIPAA. This enables organizations to demonstrate compliance with industry regulations and best practices.
LogPoint SaaS is delivered as a fully managed service, which means that customers do not need to install or manage any software or hardware. The solution is scalable and flexible, allowing organizations to easily adapt to changing security requirements and environments.

⇒ Differences Between SaaS and Logpoint SIEM and SOAR
Logpoint is a security information and event management (SIEM) and security orchestration, automation, and response (SOAR) platform that offers both SaaS and on-premise deployment options. Here are the key differences between Logpoint SaaS and Logpoint SIEM and SOAR:
- Deployment: Logpoint SaaS is a cloud-based deployment option where the platform is hosted and managed by Logpoint, while Logpoint SIEM and SOAR can be deployed on-premise, in a private cloud, or in a hybrid environment.
- Maintenance and updates: With Logpoint SaaS, Logpoint is responsible for maintaining and updating the platform, while with Logpoint SIEM and SOAR, the organization is responsible for maintaining and updating the platform.
- Scalability: Logpoint SaaS provides scalability and can easily accommodate the changing needs of an organization, while Logpoint SIEM and SOAR requires additional hardware and infrastructure to scale up.
- Access to features: Logpoint SaaS offers access to all Logpoint features, including SIEM and SOAR capabilities, out of the box. With Logpoint SIEM and SOAR, organizations need to purchase licenses and configure the platform to access the full range of features.
- Integration capabilities: Both Logpoint SaaS and Logpoint SIEM and SOAR offer integration capabilities with other security tools and technologies, but Logpoint SIEM and SOAR offers more extensive customization options for integrating with third-party solutions.
In summary, Logpoint SaaS is a cloud-based deployment option that provides a fully-managed SIEM and SOAR platform with access to all features, while Logpoint SIEM and SOAR provides more customization options and can be deployed on-premise or in a hybrid environment. The choice between the two options depends on an organization's specific needs, resources, and security requirements.

⇒ LogPoint SaaS Use Cases
LogPoint is a security information and event management (SIEM) solution that provides a cloud-based SaaS (Software-as-a-Service) offering. Some of the use cases for LogPoint SaaS include:
- Threat Detection and Response: LogPoint SaaS can be used to detect and respond to security threats in real-time. The platform can analyze logs and events from various sources such as firewalls, intrusion detection systems, and endpoints to identify potential security incidents.
- Compliance Monitoring: LogPoint SaaS can help organizations to achieve compliance with various regulatory requirements such as GDPR, HIPAA, and PCI DSS. The platform can generate reports and alerts to notify organizations of compliance violations.
- Network and Infrastructure Monitoring: LogPoint SaaS can provide real-time monitoring of network and infrastructure components such as routers, switches, and servers. The platform can detect performance issues and outages and provide alerts and notifications to help organizations quickly resolve issues.
- Insider Threat Detection: LogPoint SaaS can help organizations to detect and respond to insider threats such as data theft or unauthorized access. The platform can analyze user activity logs to identify suspicious behavior and provide alerts and reports to security teams.
- Cloud Security Monitoring: LogPoint SaaS can be used to monitor and secure cloud-based infrastructure such as AWS and Microsoft Azure. The platform can provide real-time visibility into cloud activity and detect security threats and vulnerabilities.
Overall, LogPoint SaaS provides organizations with a comprehensive SIEM solution that can help them to improve their security posture, achieve compliance, and detect and respond to security threats in real-time.

⇒ Advanced Vision IT Ltd Cybersecurity Products & Software
To build good cybersecurity protection, you need physical products and software that will help strengthen your network against attacks. If you want to view some of the ADVANCED VISION IT's cyber protection solutions, click on the links below.
- Endpoint security and antivirus software - offer a centralized management system from which security administrators can monitor, protect, and investigate vulnerabilities across all endpoints, including computers, mobile devices, servers, and connected devices. Antivirus software helps keep a computer system healthy and free of viruses and other types of malware.
- Employee Monitoring Solution - Employee monitoring solutions are software tools that enable employers to monitor the activities of their employees while they are at work. These solutions can be used to track employees' computer usage, including their internet browsing history, email communication, keystrokes, and application usage.
- Cybersecurity Backup - A backup is a copy of the system or network's data for file restoration or archival purposes. Backups are an essential part of a continuity of operations plan as they allow for data protection and recovery.
- Еmail Protection - refers to technology designed to prevent, detect and respond to cyber-attacks delivered through email. The term covers everything from gateways email systems to user behavior to related support services and security tools.
- Password Vault Manager - A password vault, password manager, or password locker is a program that stores usernames and passwords for multiple applications securely and in an encrypted format. Users can access the vault via a single “master” password.
- Vulnerability Assessment & Patch Management - The main difference between patch management and vulnerability management is that patch management is the operational process of applying remediations (patches) to vulnerable systems. Vulnerability management is the process of identifying, scanning, and prioritizing vulnerabilities for remediation.
- Data loss prevention (DLP) - makes sure that users do not send sensitive or critical information outside the corporate network.
- Cloud Security - Cloud security is a collection of security measures designed to protect cloud-based infrastructure, applications, and data. These measures ensure user and device authentication, data and resource access control, and data privacy protection.
- Next-Generation Firewall - protects your network by filtering traffic and acting as a guard between your internal network and the rest of the world. Without a Firewall, your business systems could be left wide open and vulnerable to attack. It also serves as another protective layer to block malicious software.
- Active Directory Security and Recovery are critical components of any organization's cybersecurity strategy. Here are some key steps that can be taken to secure and recover Active Directory.
- SIEM & SOAR - SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) are both tools used in cybersecurity to monitor and respond to security threats.
CONTACT OUR TEAM OF PROFESSIONALS FOR A COMPLETELY FREE CONSULTATION
CLAIM YOUR FREE IT AUDIT & CONSULTATION SCHEDULE A CALL WITH OUR TEAM

























